Public key Cryptography and message authentication ✅ Chi Tiết
Thủ Thuật Hướng dẫn Public key Cryptography and message authentication Chi Tiết
Bùi Đức Thìn đang tìm kiếm từ khóa Public key Cryptography and message authentication được Update vào lúc : 2022-10-26 23:00:09 . Với phương châm chia sẻ Bí quyết về trong nội dung bài viết một cách Chi Tiết Mới Nhất. Nếu sau khi Read nội dung bài viết vẫn ko hiểu thì hoàn toàn có thể lại phản hồi ở cuối bài để Tác giả lý giải và hướng dẫn lại nha.In the last chapter, we discussed the data integrity threats and the use of hashing technique to detect if any modification attacks have taken place on the data.
Nội dung chính Show- Message
Authentication Code (MAC)Limitations of MACHow public key cryptography is used for authentication?Is public key used for authentication?How does a public key encrypt a message?What is difference between PKI and public key cryptography?
Another type of threat that exist for data is the lack of message authentication. In this threat, the user is not sure about the originator of the message. Message authentication can be provided using the cryptographic techniques that use secret keys as done in case of encryption.
Message Authentication Code (MAC)
MAC algorithm is a symmetric key cryptographic technique to provide message authentication. For establishing MAC process, the sender and receiver share a symmetric key K.
Essentially, a MAC is an encrypted checksum generated on the underlying message that is sent along with a message to ensure message authentication.
The process of using MAC for authentication is depicted in the following illustration −
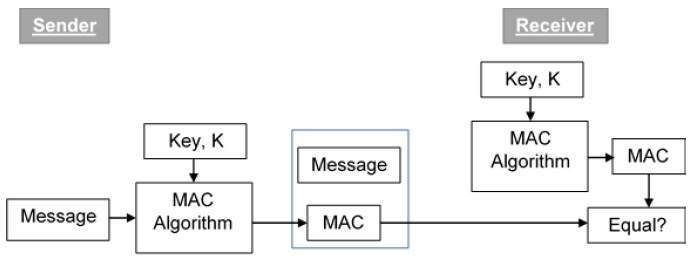
Let us now try to understand the entire process in detail −
The sender uses some publicly known MAC algorithm, inputs the message and the secret key K and produces a MAC value.
Similar to hash, MAC function also compresses an arbitrary long input into a fixed length output. The major difference between hash and MAC is that MAC uses secret key during the compression.
The sender forwards the message along with the MAC. Here, we assume that the message is sent in the clear, as we are concerned of providing message origin authentication, not confidentiality. If confidentiality is required then the message needs encryption.
On receipt of the message and the MAC, the receiver feeds the received message and the shared secret key K into the MAC algorithm and re-computes the MAC value.
The receiver now checks equality of freshly computed MAC with the MAC received from the sender. If they match, then the receiver accepts the message and assures himself that the message has been sent by the intended sender.
If the computed MAC does not match the MAC sent by the sender, the receiver cannot determine whether it is the message that has been altered or it is the origin that has been falsified. As a bottom-line, a receiver safely assumes that the message is not the genuine.
Limitations of MAC
There are two major limitations of MAC, both due to its symmetric nature of operation −
Establishment of Shared Secret.
It can provide message authentication among pre-decided legitimate users who have shared key.
This requires establishment of shared secret prior to use of MAC.
Inability to Provide Non-Repudiation
Non-repudiation is the assurance that a message originator cannot deny any previously sent messages and commitments or actions.
MAC technique does not provide a non-repudiation service. If the sender and receiver get involved in a dispute over message origination, MACs cannot provide a proof that a message was indeed sent by the sender.
Though no third party can compute the MAC, still sender could deny having sent the message and claim that the receiver forged it, as it is impossible to determine which of the two parties computed the MAC.
Both these limitations can be overcome by using the public key based digital signatures discussed in following section.
When the two parties communicate to each other to transfer the intelligible or sensible message, referred to as plaintext, is converted into apparently random nonsense for security purpose referred to as ciphertext.
Encryption:
The process of changing the plaintext into the ciphertext is referred to as encryption.
The encryption process consists of an algorithm and a key. The key is a value independent of the
plaintext.
The security of conventional encryption depends on the major two factors:
Once the ciphertext is produced, it may be transmitted. The Encryption algorithm will produce a different output depending on the specific key being used the time. Changing the key changes the output of the algorithm.
Once the ciphertext is produced, it may be transmitted. Upon
reception, the ciphertext can be transformed back to the original plaintext by using a decryption algorithm and the same key that was used for encryption.
Decryption:
The process of changing the ciphertext to the plaintext that process is known as decryption.
Public Key Encryption : Asymmetric is a form of Cryptosystem in which encryption and decryption are performed using different keys-Public key (known to everyone) and Private key (Secret key). This is known as Public Key Encryption.
Difference between Encryption and Public-key Encryption:
basis Encryption Public-Key Encryption Required for Work:- Same algorithm with the same key is used for encryption and decryption.The sender and receiver must share the algorithm and key.
- One algorithm is used for encryption and a related algorithm decryption with pair of keys, one for encryption and other for decryption.Receiver and Sender must each have one of the matched pair of keys (not identical) .
- Key must be kept secret.If the key is secret, it is very impossible to decipher message.Knowledge of the algorithm plus samples of ciphertext must be impractical to determine the key.
- One of the two keys must be kept secret.If one of the key is kept secret, it is very impossible to decipher message.Knowledge of the algorithm plus one of the keys plus samples of ciphertext must be impractical to determine the other key.
Characteristics of Public Encryption key:
- Public key Encryption is important because it is infeasible to determine the decryption key given only the knowledge of the cryptographic algorithm and encryption key.Either of the two key (Public and Private key) can be used for encryption with other key used for decryption.Due to Public key cryptosystem, public keys can be freely shared, allowing users an easy and
convenient method for encrypting content and verifying digital signatures, and private keys can be kept secret, ensuring only the owners of the private keys can decrypt content and create digital signatures.The most widely used public-key cryptosystem is RSA (Rivest–Shamir–Adleman). The difficulty of finding the prime factors of a composite number is the backbone of RSA.
Example:
Public
keys of every user are present in the Public key Register. If B wants to send a confidential message to C, then B encrypt the message using C Public key. When C receives the message from B then C can decrypt it using its own Private key. No other recipient other than C can decrypt the message because only C know C’s private key.
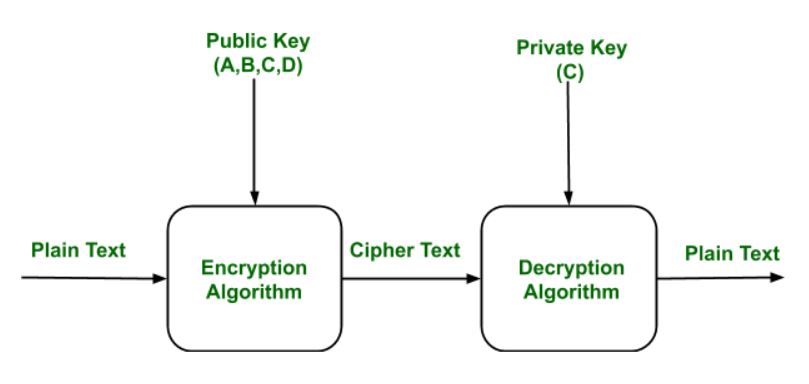
Components of Public Key Encryption:
- Plain Text:
This is the message which is readable or understandable. This message is given to the Encryption algorithm as an input.Cipher Text:
The cipher text is produced as an output of Encryption algorithm. We cannot simply understand this message.Encryption Algorithm:
The encryption algorithm is used to convert plain text into cipher text.Decryption Algorithm:
It accepts the cipher text as input and the matching key (Private Key or Public key) and produces the original plain textPublic and Private Key:
One key either Private key (Secret key) or Public Key (known to everyone) is used for encryption and other is used for decryption
Weakness of the Public Key Encryption:
- Public key Encryption is vulnerable to Brute-force attack.This
algorithm also fails when the user lost his private key, then the Public key Encryption becomes the most vulnerable algorithm.Public Key Encryption also is weak towards man in the middle attack. In this attack a third party can disrupt the public key communication and then modify the public keys.If user private key used for certificate creation higher in the PKI(Public Key Infrastructure) server hierarchy is compromised, or accidentally disclosed, then a “man-in-the-middle
attack” is also possible, making any subordinate certificate wholly insecure. This is also the weakness of Public key Encryption.
Applications of the Public Key Encryption:
- Encryption/Decryption:
Confidentiality can be achieved using Public Key Encryption. In this the Plain text is encrypted using receiver public key. This will ensures that no one other than receiver private key can decrypt the cipher text.Digital signature:
Digital signature is for senders authentication purpose. In this sender encrypt the plain text using his own private key. This step will make sure the authentication of the sender because receiver can decrypt the cipher text using senders pubic key only.Key exchange:
This algorithm can use in both Key-management and securely transmission of data.
How public key cryptography is used for authentication?
The public key authentication protocol uses two keys per node, a public key for encryption and a private key for decryption. Everybody has access to the public key of a node, while the private key is secret. During authentication, random numbers are generated and exchanged, similar to the shared secret key protocol.Is public key used for authentication?
In public key authentication, the scheme is based on public key cryptography, using cryptosystems where encryption and decryption are done using separate keys, and it is not feasible to derive the decryption key from the encryption key. Each user creates a public/private key pair for authentication purposes.How does a public key encrypt a message?
Public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the public key, available for anyone to use. The other key is known as the private key. Data encrypted with the public key can only be decrypted with the private key.What is difference between PKI and public key cryptography?
In public-key cryptography, two keys are used, one key is used for encryption, and the other is used for decryption. 3. In private key cryptography, the key is kept a secret. In public-key cryptography, one of the two keys is kept a secret. Tải thêm tài liệu liên quan đến nội dung bài viết Public key Cryptography and message authentication Public key cryptography